Over half of Internet users get at least one phishing email each day, which can potentially expose a company’s network to a security risk if not handled properly. Understandably, protecting a company’s network from this fraudulent practice is top of mind for many IT professionals. Kindly follow below the steps of how to enable DKIM, a security technology that customers can use to protect their networks.
“When working with customers moving off of other platforms to Office 365, we’re frequently asked if Microsoft supports DomainKeys Identified Mail (DKIM) on Office 365. The good news – and the short news – is yes, it does. Exchange Online Protection (EOP) filters every single mailbox on Office 365 and provides even better protection than has previously been supported in IPv6,” says Williams.
What is DKIM?
DomainKeys Identified Mail (DKIM) is a technology that reduces email spoofing, a form of communication identity fraud that can lead to increased spam and more intensified phishing campaigns. When an email server is configured to use DKIM, this allows an organization to show responsibility for the mail message through encrypted keys. Configuring DKIM can significantly reduce the risk of spoofed emails by providing a mechanism that allows receiving mail servers to check that the message is from a trusted or authorized server, and that the message has not been modified during its transport. Office 365, using ForeFront Online Protection, previously allowed DKIM when using IPv6, but it was later removed while migration to Exchange Online Protection. But, great news, it is now back. To learn more about the history of DKIM, Microsoft has provided a great blog post here.
How Do I Set Up DKIM?
Let’s get Office 365 setup to support DKIM. This must be done for each domain you wish to enable for DKIM.
First, for each domain, you will need to create TWO CNAME records in your PUBLIC DNS Zone. To build the CNAME records, you will use the following format:
selector1-<domainGUID>._domainkey.<inititalDomain>
The <domainGUID> will be the first part of the MX record as listed for Exchange Online. For example, to enable Domain Name yourdomainname.com for DKIM, I will look up the MX record, and I see the MX record points to:
yourdomainname.com
MX preference = 0
mail exchanger = yourdomainname-com.mail.protection.outlook.com
We take the first part, yourdomainname-com, and leave off the .mail.protection.outlook.com.
The <InitialDomain> is the prefix part of your tenant name. In my case, my tenant domain is yourdomainname.onmicrosoft.com. So, the <initialdomain> is yourdomainname in this example.
Now, to see it all together, we would build this as follows:
selector1._domainkey.yourdomainname.com. CNAME selector1-yourdomainname-com._domainkey.yourdomainname.onmicrosoft.com
selector2._domainkey.yourdomainname.com. CNAME selector2-yourdomainname-com._domainkey.yourdomainname.onmicrosoft.com
Once you have the DNS records in place and have verified they are publicly accessible, you can open a remote PowerShell session to Exchange Online.
Now, let’s enable DKIM for our domain:
Type: New-DkimSigningConfig –DomainName yourdomainname.com –Enabled $true
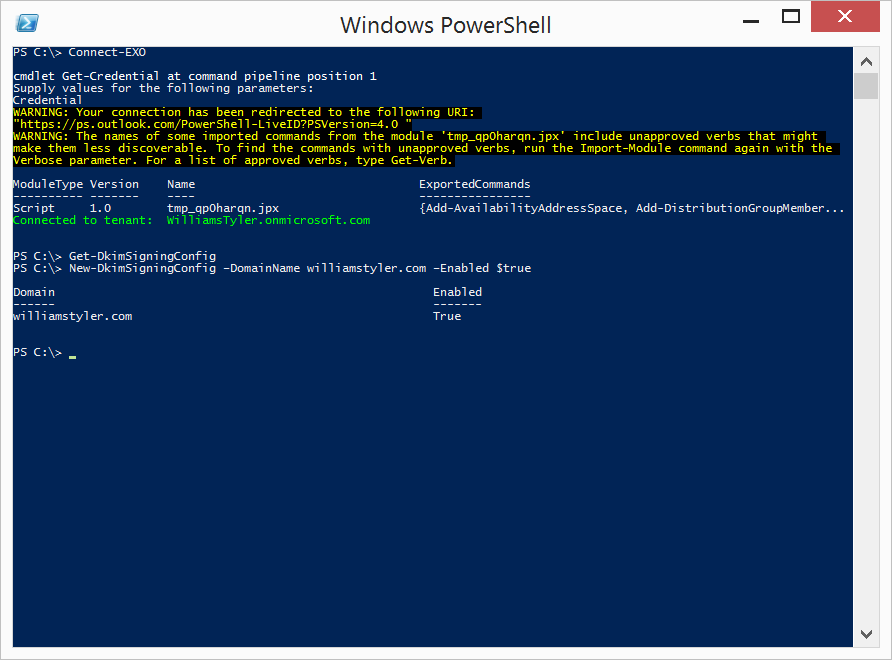
Now, let’s ensure the output shows Enabled = True.
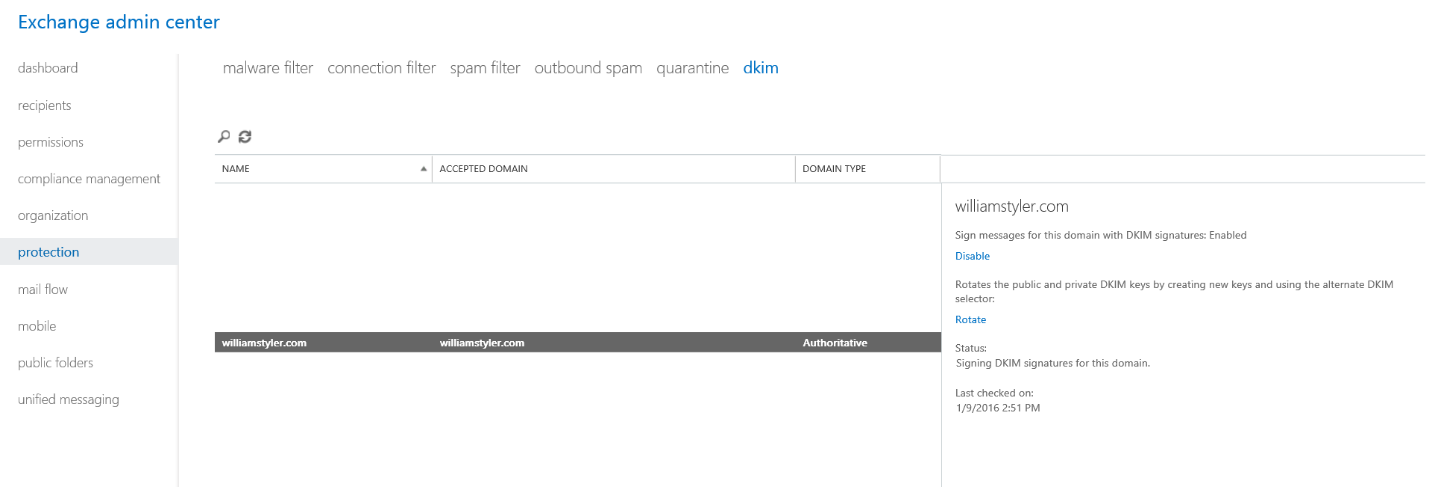
Finally, let’s open the Exchange Admin Center, and navigate to the DKIM tab under Protection to make sure it’s set up correctly. On the right side, under yourdomainname.com you’ll see that it confirms it’s enabled.
Comments
Article is closed for comments.